Malware Forensics: 

Investigating and Analyzing Malicious Code
windows Tools 

July 10, 2009:
FEATURED TOOLS: Procdump- SysInternals' new process memory acquisition tool
Microsoft (who acquired Sysinternals in July, 2006) has recently released a process memory acquisition/dumping tool, ProcDump. Below is the usage menu and an example of acquiring the memory of a target process.
C:\Users\MalwareLab>procdump
ProcDump v1.0 - Writes process dump files
Copyright (C) 2009 Mark Russinovich
Sysinternals - www.sysinternals.com
Monitors a process and writes a dump file when the process exceeds the
specified CPU usage.
usage: procdump [-c CPU usage [-u] [-s seconds] [-n exceeds]] [-h] [-e] [-ma] [-
r] [-o] [[<process name or PID> [dump file]] | [-x <image file> <dump file> [arg
uments]]
-c CPU threshold at which to create a dump of the process.
-e Write a dump when the process encounters an unhandled exception.
-h Write dump if process has a hung window.
-ma Write a dump file with all process memory. The default
dump format includes thread and handle information.
-n Number of dumps to write before exiting.
-o Overwrite an existing dump file.
-r Reflect (clone) the process for the dump to minimize the time
the process is suspended (Windows 7 and higher only).
-s Consecutive seconds CPU threshold must be hit before dump is
written (default is 10).
-u Treat CPU usage relative to a single core.
-x Launch the specified image with optional arguments.
To just create a dump of a running process, omit the CPU threshold. If
you omit the dump file name, it defaults to <processname>.dmp.
Example: Write up to 3 dumps of a process named 'consume' when it exceeds 20% CPU usage for three seconds to the directory c:\dump\consume with the name consume.dmp:
C:\>procdump -c 20 -n 3 -o consume c:\dump\consume
Example: Write a dump for a process named 'hang.exe' when one of it's windows is unresponsive for more than 5 seconds:
C:\>prodcump -h hang.exe hungwindow.dmp
Example: Launch a process and then monitor it for excessive CPU usage:
C:\>procdump -c 30 -s 10 -x consume.exe consume.dmp
Example: Write a dump of a process named 'iexplore' to a dump file that has the default name iexplore.dmp:
C:\>procdump iexplore
In the following example, I used ProcDump to dump the process memory of Firefox to a file:
C:\Users\MalwareLab>procdump -ma firefox
ProcDump v1.0 - Writes process dump files
Copyright (C) 2009 Mark Russinovich
Sysinternals - www.sysinternals.com
Writing dump file C:\Users\MalwareLab\firefox.dmp...
The process dumps generated by procdump are .dmp files, providing for a variety of different parsing and analysis options.
July 5, 2009:
FEATURED TOOLS: Shock Wave Flash Malware Analysis Tools
SWFScan- HP SWFScan, a free tool developed by HP Web Security Research Group, will automatically find security vulnerabilities in applications built on the Flash platform. How SWFScan works and what vulnerabilities it finds:
- Decompiles applications built on the Adobe Flash platform to extract the ActionScript code and statically analyzes it to identify security issues such as information disclosure.
- Identifies and reports insecure programming and deployment practices and suggests solutions.
- Enables you to audit third party applications without requiring access to the source code.
- PDF2SWF A PDF to SWF Converter. Generates one frame per page. Enables you to have fully formatted text, including tables, formulas, graphics etc. inside your Flash Movie. It's based on the xpdf PDF parser from Derek B. Noonburg.
- SWFCombine A multi-function tool for inserting SWFs into Wrapper SWFs, contatenating SWFs, stacking SWFs or for basic parameter manipulation (e.g. changing size).
- SWFStrings Scans SWFs for text data.
- SWFDump Prints out various informations about SWFs, like contained images/fonts/sounds, disassembly of contained code as well as cross-reference and bounding box data.
- JPEG2SWF Takes one or more JPEG pictures and generates a SWF slideshow from them. Supports motion estimation compression (h.263) for better compression of video sequences.
- PNG2SWF Like JPEG2SWF, only for PNGs.
- GIF2SWF Converts GIFs to SWF. Also able to handle animated gifs.
- WAV2SWF Converts WAV audio files to SWFs, using the L.A.M.E. MP3 encoder library.
- AVI2SWF Converts AVI animation files to SWF. It supports Flash MX H.263 compression. Some examples can be found at examples.html. (Notice: this tool is not included anymore in the latest version, as ffmpeg or mencoder do a better job nowadays)
- Font2SWF Converts font files (TTF, Type1) to SWF.
- SWFBBox Allows to read out, optimize and readjust SWF bounding boxes.
- SWFC A tool for creating SWF files from simple script files. Includes support for both ActionScript 2.0 as well as ActionScript 3.0.
- SWFExtract Allows to extract Movieclips, Sounds, Images etc. from SWF files.
- AS3Compile A standalone ActionScript 3.0 compiler. Mostly compatible with Flex.
Flasm- Flasm disassembles your entire SWF including all the timelines and events. Looking at disassembly, you learn how the Flash compiler works, which improves your ActionScript skills. You can also do some optimizations on the disassembled code by hand or adjust the code as you wish. Flasm then applies your changes to the original SWF, replacing original actions.
Flare- Flare is a freeware ActionScript decompiler. Flare processes an SWF and extracts all scripts to a single text file. Only ActionScript is extracted! Available for Windows, Mac OS X and Linux.
Swifty- Swifty Utilities are a set of SWF applications written by Burak Kalayci. The tools include:
- [Swifty] UnlockSWF, can add or remove protection, add/remove or reset debugging option to SWF files.
- Swifty Compress and Swifty Uncompress, can compress and decompress SWF files.
- Swifty Batch Projector Creator, Drag & drop Batch SWF to Exe converter.
- Swifty Xena Pro, extracts SWF files embedded in applications, including Flash.exe, Aftershock.exe, any standalone projector and Director movies. (Can optionally replace them!). Also can extract DXR/CXT files embedded in Director projectors.
- Swifty Hercules-extracts movie clips (sprites) from SWF files as SWF files.
- Swifty Zeus-extracts each layer in a SWF as a seperate SWF. Intended for viewing the layer structure.
- Swiffer (Swifty Sniffer), does nothing useful other than listing the tags in the SWF file and removing the tags you like (including the protect tag!). Also Swiffer lets you see the header information, i.e. the frame rate and the pixel size of the animation. For removing protection only use the new Swifty Unprotector, Swiffer can sometimes produce SWFs that crash Flash. Use UnlockSWF for unprotection needs...
- Swifty Unprotector, Drag & drop SWF protection remover. Use UnlockSWF for unprotection needs...
DComsoft- Dcomsoft offers a number of SWF utilities
- SWF Protector- an encryption solution to protect Flash files from SWF decompilers.
- SWF Protect Remover
- Dump Flash Decompiler
- SWF Picture Extractor
ScriptSWF (SSWF)- A C and C++ Library + a compiler to create Adobe Flash SWF movies up to version 9 (v1.8.1). Supports nearly all the tags, includes an ActionScript compiler. Detailed docs and other tools: convert fonts to Flash, decompile Flash, jpg2swf.
Tamarin/ActionScript Byte Code Decompiler- Tamarin tools include an actionscript byte code (abc) decompiler, which can generate readable pseudocode from swf or abc files.
SoThink SWF Decompiler- a Flash decompiler that decompiles one or more SWF to FLA, SWF to FLEX project. It supports Flash 6, Flash MX 2004, Flash 8, Flash CS3 and Flash CS4. This Flash decompiler with multi-language can recover FLA/FLEX project, extract elements including shape, sounds, images, sprites, fonts, texts, ActionScript etc.
SWF Reader- SWF Reader is a program to unprotect encrypted swf files.
Main features:
- Remove/add tags.
- Manipulate doABC structure (AS3).
- Full unprotect AS2 files which are encrypted by SWF Encrypt 5.
- Unprotect AS3 files which are encrypted by SWF Encrypt 5. There is not possible to recover names (class, vars, functions) because encrypter remove original names irretrievably.
April 9, 2009:

FROM THE ARCHIVES: WinTasks Professional
WinTasks Professional was a process analysis tool previously offered by UniBlue (formerly liutilities); copies of the utility are still floating around on the Internet for download with uncertain reliability. Rich with functionality, WinTasks gave the user a detailed main console and the ability to gather more granular information about a particular process through numerous sub-windows. One of the more unique features of WinTasks versus other process analysis tools is that it tapped into the Uniblue/liutiltiies process library; with this feature, if a particular process was cataloged, a brief description would be provided in the lower right pane of the main interface (Uniblue also offers a DLL and File Extension Libraries).

Sub-windows that provided a more detailed view of a selected process included:
1) Modules- Provided a listing of the DLLs loaded/invoked by the process

2) Windows- identified all windows owned by a selected process, including minimized, normal and maximized windows.
3) Autostart- This window revealed programs that were set to start automatically when booting the target computer.
4) Statistics- Revealed CPU use and memory consumption by a selected process

5) Logging- WinTasks automatically logged information about all processed that were started or stopped, providing the digitial investigator with a "playbook" of what occurred on the target system.
6) Process Library Details

April 9, 2009:
FEATURED TOOLS: PDF File Parsing and Analysis
PDFiD (pdfid.py)- Wrtitten by malware analyzing maestro Didier Stevens, this tool is not a PDF parser, but it will scan a file to look for certain PDF keywords, allowing you to identify PDF documents that contain (for example) JavaScript or execute an action when opened. PDFiD will also handle name obfuscation. The idea behind the tool is to use it first to triage PDF documents, and then analyze the suspicious ones with Didier's pdf-parser.
PDF-parser (pdf-parser.py)- Written by Didier Stevens, this tool will parse a PDF document to identify the fundamental elements used in the analyzed file. You can see the parser in action in this screencast.
PDFMiner-Python PDF parser and analyzer. "PDFMiner is a suite of programs that aims to help analyzing text data from PDF documents. It includes a PDF parser, a PDF renderer (though only rendering text is supported for now), and a couple of nice tools to extract texts. Unlike other PDF-related tools, it allows to obtain the exact location of texts in a page, as well as other layout information such as font size or font name, which could be useful for analyzing the document. It also infers text running within a page by using clustering technique.
Features:
- Written entirely in Python. (for version 2.5 or newer)
- PDF-1.7 specification support.
- Non-ASCII languages and vertical writing scripts support.
- Various font types (Type1, TrueType, Type3, and CID) support.
- Basic encryption (RC4).
- PDF to HTML conversion (with a sample converter web app).
- Outline (TOC) extraction.
- Tagged contents extraction."
March 14, 2009:
FEATURED TOOL: Computer Aided Investigative Environment (CAINE)
CAINE (Computer Aided Investigative Environment) is a GNU/Linux live distribution created by Giancarlo Giustini as a project of Digital Forensics for Interdepartment Center for Research on Security, supported by the University of Moderna and Reggio Emilla. CAINE includes a Linux bootable environment as well as a Live Windows environment utilizing WinTaylor, a new forensic interface built for Windows.
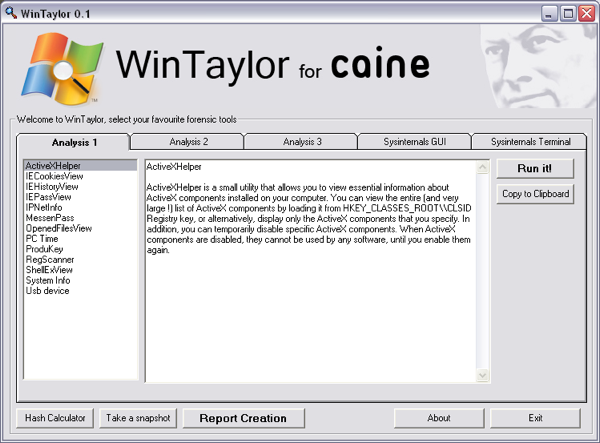
January 17, 2009:
FEATURED TOOL: Malware Analysis Frameworks
There are a number of freely available malware analysis frameworks that enable a user to conduct automated dynamic analysis of suspicious executable files. Some of these frameworks include:
The Reusable Unknown Malware Analysis Net ("TRUMAN")- Developed by venerable malware researcher Joe Stewart of Secureworks (formerly of LURQ), "Truman can be used to build a "sandnet", a tool for analyzing malware in an environment that is isolated, yet provides a virtual Internet for the malware to interact with. It runs on native hardware, therefore it is not stymied by malware which can detect VMWare and other VMs. The major stumbling block to not using VMs is the difficulty involved with repeatedly imaging machines for re-use. Truman automates this process, leaving the researcher with only minimal work to do in order to get an initial analysis of a piece of malware.
Truman consists of a Linux boot image (originally based on Chas Tomlin's Windows Image Using Linux) and a collection of scripts. Also provided is pmodump, a Perl-based tool to reconstruct the virtual memory space of a process from a PhysicalMemory dump. With this tool it is possible to circumvent most packers to perform strings analysis on the dumped malware."
Automated aNalysis and Network emulation ("ANNE")- Developed by the Luxembourg Computer Security Research & Response Team, ANNE Is a framework to analyze unknown binaries in an automated fashion. More information can be found at Malware/Anne_-_release_0.1
ANNE is composed of
- backend xmlserver
- a daemon that process the jobs
- UML (user mode linux) Malware/UML Howto for ANNE
- a web interface frontend
- simulation scripts that run inside the UML
Zero-Wine- Authored by Joxean Koret, "Zero wine is an open source (GPL v2) research project to dynamically analyze the behavior of malware. Zero wine just runs the malware using WINE in a safe virtual sandbox (in an isolated environment) collecting information about the APIs called by the program. The tool is distributed as a prebuilt QEmu virtual machine (or in source code form)."
January 1, 2009:
ChromeCacheView: Released in October 2008 (with additional releases in other languages through December 2008) "ChromeCacheView is a small utility that reads the cache folder of Google Chrome Web browser, and displays the list of all files currently stored in the cache. For each cache file, the following information is displayed: URL, Content type, File size, Last accessed time, Expiration time, Server name, Server response, and more. You can easily select one or more items from the cache list, and then extract the files to another folder, or copy the URLs list to the clipboard."
Dltrace: developed by iDefense Labs, dltrace is "a dynamic library call tracer which attempts to remain portable to all x86 platforms that support ELF binaries and expose a debugging interface via procfs or the ptrace() system call. The shared library call tracing is done at a level which allows calls to all symbols exported by loaded libraries to be traced. In addition, dltrace does not rely on rtld symbols to retrieve library and symbol information and is capable of determing function arguments dynamically via run-time disassembly."
December 28, 2008:
BotHunter: In November, 2008, SRI International released BotHunter v.1, a passive network monitoring tool designed to recognize the communication patterns of malware-infected computers within a network perimeter. Available for Windows and *nix platforms (as well a Bootable CD), SRI International describes BotHunter as "an application designed to track the two-way communication flows between internal assets and external entities, developing an evidence trail of data exchanges that match a state-based infection sequence model. BotHunter consists of a correlation engine that is driven by a customized and augmented release of Snort version 2, which tracks the underlying actions that occur during the malware infection process: inbound scanning, exploit usage, egg downloading, outbound bot coordination dialog, outbound attack propagation, and malware P2P communication. The BotHunter correlator then ties together the dialog trail of inbound intrusion alarms with those outbound communication patterns that are highly indicative of successful local host infection. When a sequence of evidence is found to match BotHunter's infection dialog model, a consolidated report is produced to capture all the relevant events and event sources that played a role during the infection process. We refer to this analytical strategy of matching the dialog flows between internal assets and the broader Internet as dialog-based correlation (patent pending)."
SRI International offers additional malware analysis resources, including the Cyber-Threat Analytics (Cyber-TA) project, Event Monitoring Enabling Responses to Anomalous Live Disturbances (EMERALD), the Malware Threat Center.
December 27, 2008:
FEATURED TOOL: Wormboy
Wormboy: Developed by David J. Malan, Lecturer on Computer Science at Harvard College for the School of Engineering and Applied Sciences, Wormboy is "a kernel-mode driver for Windows XP with Service Pack 2 that inserts hooks into _KeServiceDescriptorTable before and after all but two system services. Inspired by Strace for NT, as well as by work by Nebbett and Dabak et al., Wormboy not only captures a call's service ID and input parameters, but also its output parameters and return value, along with a caller's name, process ID, thread ID, and mode." (Papers relating to Wormboy can be found here)
December 15, 2008:
Mandiant Memoryze: MANDIANT has released "Memoryze," free memory forensic software that helps incident responders find malicious code artifacts in live memory. Results can natively be loaded for review in Internet Explorer or Excel, or alternatively, in Peter Silberman's Audit Viewer GUI.
Using MalZilla to analyze malicious web sites: MalZilla is a useful program for use in exploring malicious pages. It allows the digital investigator to choose his own user agent and referrer, and has the ability to implement proxies; It also shows the digital investigator the full source of webpages and all the HTTP headers.
December 14, 2008:
Windows SteadyState v. 2.5: Another software option for "baselineling" a malware lab environment is Windows SteadyState (available for Windows XP and Vista).
Virus Total updates: Virus Total, the online malicious code scanning service, has added some great features to its scanning engines and output, including packing detection with PEiD; file identification using Marco Pontello's Trid; PE structure information output, and contextual piecewise hashing using Jesse Kornblum's ssdeep. It would be interesting if Virus Total used the matching functionality of ssdeep to compare a submitted specimen with previous submissions and provided output identifying related/similar specimens.

September 9, 2008:
Over the last few months NirSoft has released a number of new freeware utilities that did not make it into the book but may make valuable additions to your malware forensics arsenal.
ProcessActivityView v.1.05- Creates a summary of all files and folders that the selected process tries to access. For each file that the process access, the following information is displayed: Number of times that the file was opened and closed, number of read/write calls, total number of read/write bytes, the dll that made the last open-file call, and more

SocketSniff v1.00- Allows the user to watch the Windows Sockets (WinSock) activity of the selected process. For each created socket, the following information is displayed: socket handle, socket type, local and remote addresses, local and remote ports, total number of send/receive bytes, and more. You can also watch the content of each send or receive call, in Ascii mode or as Hex Dump.
RegFromApp v1.07- monitors the Registry changes made by the application that you selected, and creates a standard RegEdit registration file (.reg) that contains all the Registry changes made by the application. You can use the generated .reg file to import these changes with RegEdit when it's needed.
DotNetResourceExtract v1.00- utility that scan dll/exe files of .NET applications, and extract all .NET embedded resources (Bitmaps, Gifs, HTML files, and so on) stored in them into the folder that you specify.
UserAssistView v1.00- This utility decrypt and displays the list of all UserAssist entries stored under HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist key in the Registry. The UserAssist key contains information about the exe files and links that you open frequently. you can save the list of UserAssist entries into text/html/xml/csv file, as well as you can delete unwanted items.
OperaCachView v1.00- a small utility that reads the cache folder of Opera Web browser, and displays the list of all files currently stored in the cache. For each cache file, the following information is displayed: URL, Content type, File size, Last accessed time, and last modified time in the server.
September 3, 2008:
SANS releases the SANS Investigative Forensic Toolkit (SIFT) Workstation, a VMware Appliance that is preconfigured with all the necessary tools to perform a forensic examination.
September 2, 2008:
OSSEC v. 1.6 is released. OSSEC is an Open Source Host-based Intrusion Detection System. It performs log analysis, integrity checking, Windows registry monitoring, rootkit detection, real-time alerting and active response.
September 2, 2008:
The Honeynet Project and School of Mathematics, Statistics and Computer Science at Victoria University of Wellington announce the release of Capture-HPC v2.5.1. Capture-HPC, a high-interaction client honeypot (or honeyclient) is an innovative security product that is able to find and investigate the increasing problem of client-side computer attacks.
September 1, 2008:
Sanderson Forensics releases RevEnge, a fully featured hex viewer designed with Reverse Engineering in mind. It comes packed with features not seen in other Hex viewers such as it ability to perform on the fly decompression of ZLib compressed data, display and search for dates in multiple date formats and decode SMS messages encoded in GSM PDU 7 bit ASCII.
August 24, 2008:
The Cryptographic Implementations Analysis Toolkit (CIAT) is released.
CIAT, written by Omar Herrera, is s a compendium of command line and graphical tools whose aim is to help in the detection and analysis of encrypted byte sequences within files (executable and non-executable). It is particularly helpful in the forensic analysis and reverse engineering of malware using cryptographic code and encrypted payloads.
The following is a quick summary of the tools included:
- CryptoLocator
CryptoLocator allows the detection of pseudo-random byte sequences within mixed content
files. It was designed specifically to detect encrypted payloads within malware executables, but
it can be used for other purposes, such as detecting encrypted communications or verifying the
output quality of closed source encryption software. Algorithms come from NIST's SP800-22.
- CryptoCodeDetector
CryptoCodeDetector is a tool specifically designed for analysis of PE executables (only 32 bit
executables are currently supported). It was created to locate code references to encrypted
payloads within malware (i.e. those identified by CryptoLocator in executable files), but it can be
used also to search for any reference to any location within a range in the file being analyzed.
- CryptoVisualizer
This is a very simple interactive tool that allows you to see graphically any file. It was designed
to aid human researchers to quickly pinpoint probably pseudorandom sequences. Of course,
this is not a robust technique, but it helps. Source code, executable code, text and other forms
of non pseudo-random content in files are also easily identifiable with this tool since bytes
forming those kind of contents tend to fall within a certain range or form visually identifiable
patterns.
- CryptoID
CryptoID is a tool that implements two algorithms: one that assesses the degree of randomness
and one that assesses the degree of encryption (for byte sequences that are found to be
random). Both are based on statistics from Fractional Fourier Transforms applied to the byte
sequences being analyzed.
The toolkit is currently available at http://sourceforge.net/projects/ciat/
August 15, 2008
Volatile Systems releases Volatility 1.3, the open source memory framework.
Widely recognized as one of the most effective memory analysis forensic tools, Volatility was recently used in the DFRWS 2008 Forensics Challenge and the Forensics Rodeo, helping win both events!
ManTech releases ManTech Memory DD 1.3
"ManTech Memory DD captures a record of physical, or random access memory which is lost when the computer is shutdown. Released at no charge under the GPL license for government and private use, ManTech’s Memory DD (MDD) is capable of acquiring memory images from the following Microsoft® products: Windows® 2000, Windows Server 2003, Windows XP®, Windows Vista®, and Windows Server 2008.ManTech’s Memory DD 1.0 acquires a forensic image of physical memory and stores it as a raw binary file. To help verify data integrity and aid in the preservation of the evidence, the information captured by ManTech Memory DD is checked by the Message-Digest algorithm 5 (MD5), the common Internet standard used in security applications. The binary file can then be analyzed using external tools to identify items of interest to the examiner."
_________________________________________________________________________________________________________________________________________